Introduction:
File permissions in Linux are a crucial aspect of system security and user management. They define who can access a file or directory and what actions (read, write, execute) they can perform. In this article, we will see a comprehensive understanding of file permissions, their components, and how to manipulate them effectively.
Components of File Permissions:
Lets understand this using an example. Create a file and do ls -ltr to check the details of file.
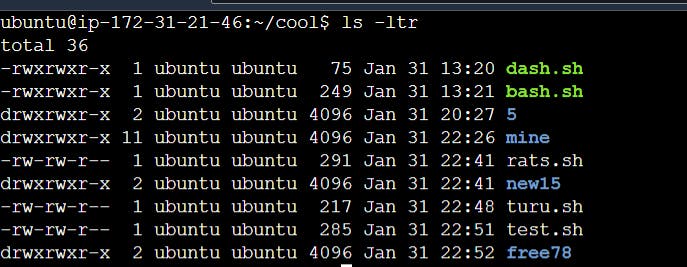
In Linux, file permissions are represented by a 10-character string, such as drwxr-xr--. Let's break down this string:
File Type: The first character represents the type of file. Common types include:
-: Regular filed: Directoryl: Symbolic link
User Permissions (Owner): The next three characters (2-4) represent permissions for the owner of the file. These can be
r(read),w(write), andx(execute).Group Permissions: The following three characters (5-7) denote permissions for the group associated with the file.
Other Permissions: The last three characters (8-10) specify permissions for others – users who are neither the owner nor part of the group.

Understanding Numeric Representation:
File permissions can also be represented using numeric values (octal format). Each permission is assigned a numeric value: r is 4, w is 2, and x is 1. The sum of these values represents the permission set.
rwx(read, write, execute) is 7 (4 + 2 + 1).rw-(read, write) is 6 (4 + 2)./r--(read) is 4.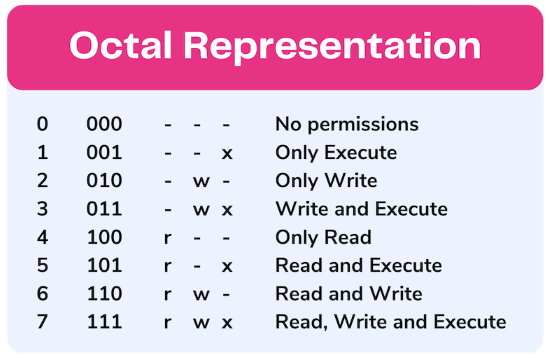
Changing File Permissions:
The chmod command is used to change file permissions. Here are some examples:
chmod +x file: Adds execute permission to the file.chmod 754 file: Assigns read, write, and execute to the owner, read and execute to the group, and read-only to others.
Changing Ownership:
The chown command changes the ownership of a file:
chown user:group file: Changes both the owner and group of the file.
Special Permissions:
Beyond the basic permissions, there are special permissions like the setuid (s), setgid (s), and sticky bit (t). The setuid and setgid bits, when set, allow the file to be executed with the permissions of the file owner or group, respectively. The sticky bit, often applied to directories, restricts file deletion to the file owner.
Access Control Lists (ACL):
ACL extends the traditional Unix file permissions model, allowing more granular control over access. ACLs are additional entries associated with a file or directory, specifying permissions for specific users or groups.
Practical Usage of ACL:
With getfacl, we can fetch the ACL information about a file or directory, and using setfacl, we can assign the ACL permissions to the file.
$ getfacl filename
$ setfacl -m u:user1:r-x filename
This example assigning "read" and "execute" permission to "user1"
Conclusion:
File permissions play a vital role in securing a Linux system. Understanding how to interpret and manipulate them is fundamental for DevOps engineers. As we delve into DevOps, mastery of both file permissions and ACL will prove invaluable for maintaining a secure and well-organized environment.
😊Happy Learning : )
